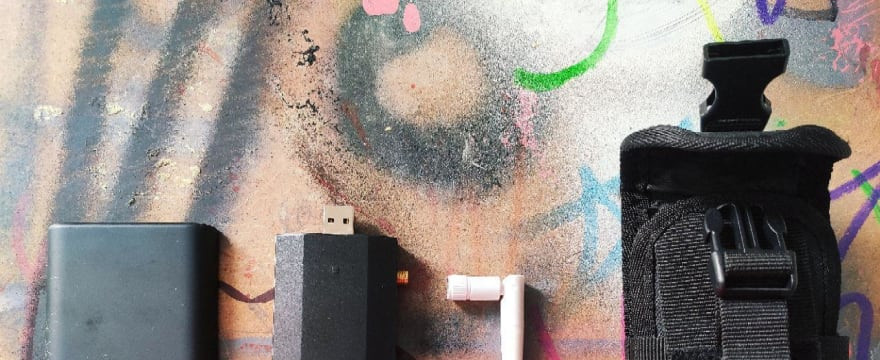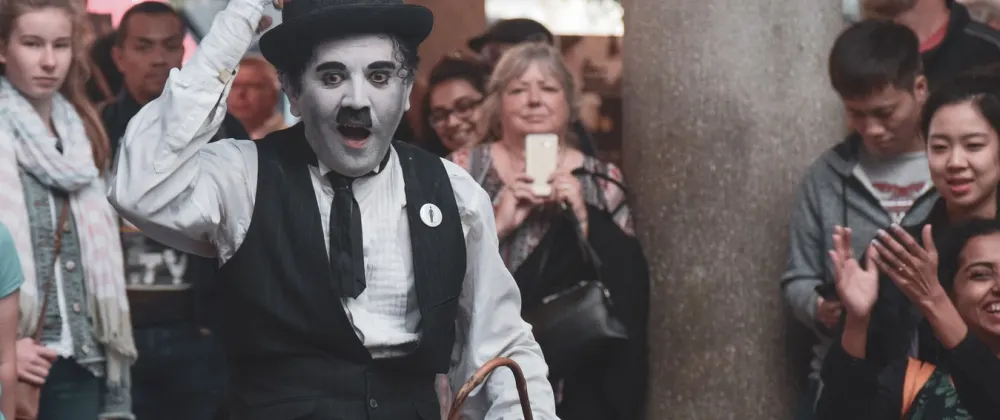
Disclaimer: All of the following information takes for granted you’ve been hired for it.
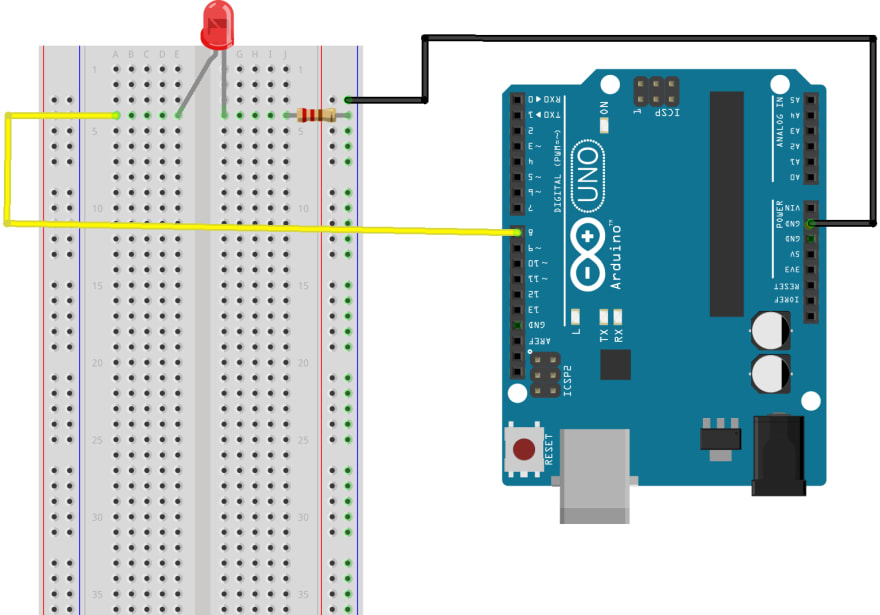
One of the best parts of offensive security is the wide range of attacks than can be performed. As the idea is to simulate a real cyberattack, there are several kind of things to do to approach the “victim”. Even most of it involves using various tools in the computer, it also implies physical access, phishing, and getting information though the users of the system. This parts involves a bit of a performance, to learn about what kind...